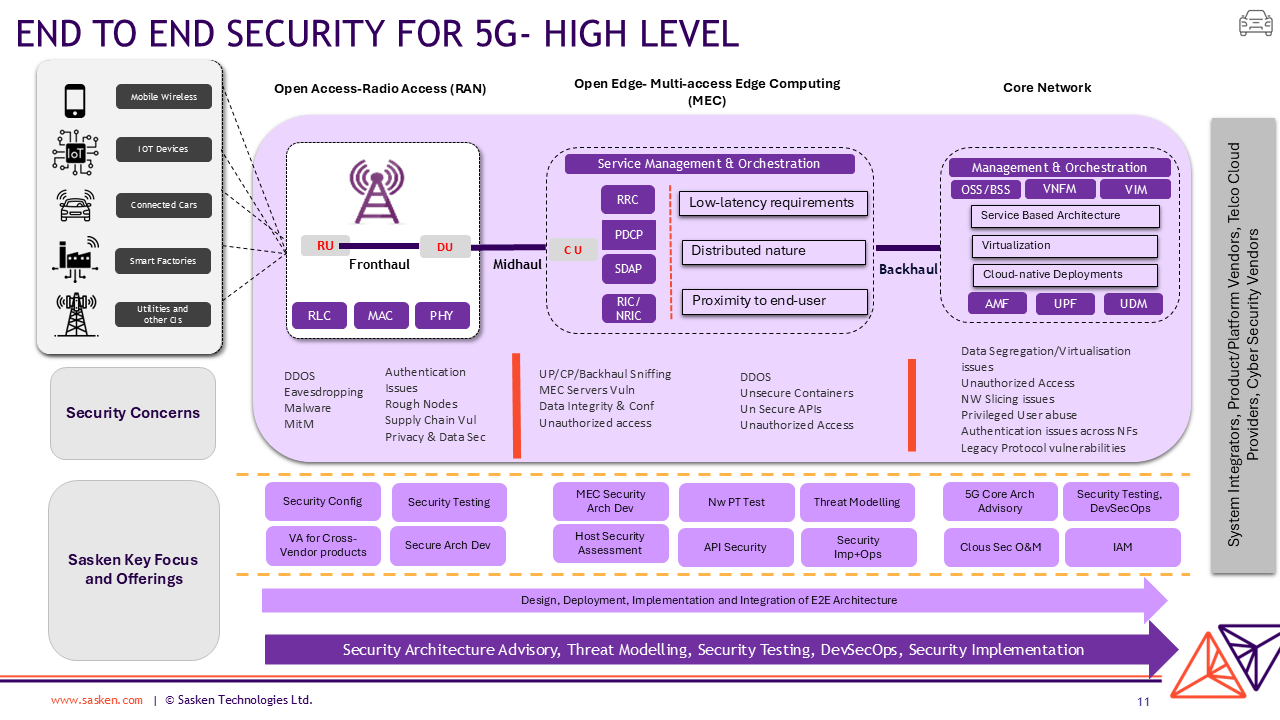
In 2G/3G, threats were focused on traditional attacks like SIM swapping and fake base stations (FBS) that mimic legitimate networks. With 4G and 5G, the attack surface has expanded from closed to hybrid systems, especially as early 5G NSA deployments rely on LTE control plane protocols and EPC, inheriting LTE vulnerabilities. The cloud-native architecture of 5G further increases security risks. Sasken takes an end-to-end architectural approach, covering O-RAN, MEC, and Core, to design, develop, and integrate security controls across the entire 5G ecosystem.
- O RAN Security: Key focus is to ensure secure communication on all interfaces based on 3GPP and O-RAN alliance specifications, implement confidentiality and Integrity on connections between O-RAN and external components and Secure communication between network functions leveraging native controls provided by RAN vendors. Sasken services cover security testing- vulnerability assessment and penetration testing for cross vendor products, Interface security testing validating secure configuration, secure architecture development to address security risks arising from authentication issues, rogue devices, DDOS (Bots) attacks, MitM, Supply chain, privacy and data corruption, Malware, Firmware hacks and so on.
- MEC layer Security: Multi-access Edge Computing in 5G introduces unique security challenges due to its distributed nature, low-latency requirements, and proximity to end-users. Sasken’s key focus areas involve, 1) securing communication between MEC applications, edge hosts, and 5G core networks through mutual authentication, federated identity management for multi-tenant environment 2) implementing zero trust architecture using micro segmentation to isolate MEC components from the Core and leveraging 5G authentication and encryption mechanism 3) Data security and privacy using strong encryption 4) Securing Edge components through Secure APIs, Secure boot and HSMs 5) implementation of threat detection and response to mitigate risk from abnormal behavior in MEC traffic 6) Supply chain security to ensure trusted hardware and software components 7) Policy and regulatory compliance particularly ETSI MEC Security Compliance and GDPR.
- The 5G core network (5GC): Introduces new security challenges due to its service-based architecture (SBA), virtualization, and cloud-native deployments. Sasken security team leveraging cloud native and telco cloud controls, helps clients in mitigating risks arising from virtualization vulnerabilities, potential cross slice attacks, improper access controls, API vulnerabilities, supply chain, Policy and regulatory compliance mandates etc. Sasken’s brings zero trust, API-first, cloud-native security approach with a strong focus on IAM, encryption, segmentation, anomaly detection, and secure cloud deployments to build security by design. Sasken’s approach supports broad categories of Secure 5G business use cases for example creating custom network in the core with unique capabilities or secure edge use cases which demand services with varied performance requirements for example, IoT, automated cars, streaming video, and remote health care.