SASKEN CYBERSECURITY SOLUTIONS:
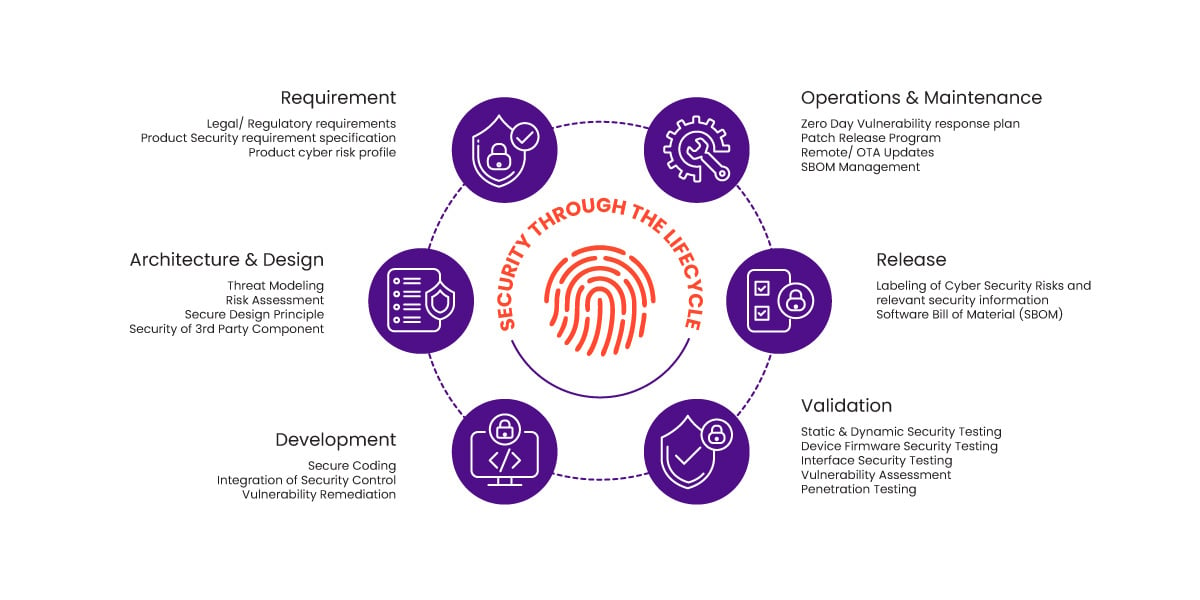
Sasken’s Cybersecurity Services enables enterprises to develop, maintain, and take digital products to the market with security postures that empower operational excellence. Through the Sasken Security Lab enterprises can leverage end-to-end vulnerability assessment & penetration testing for hardware and software products including consumer devices, automotive and transport, industrial (IIOT, Industry 4.0), web applications, mobile applications, wireless communication interfaces, network, and cloud.
Whether you are building the foundation of your digital product or have already released the beta version in the market, we help you counter risks and re-engineer business security for a dynamic business environment.